
Agent-based scanning is getting less relevant because modern cloud-native elastic workloads are too fast-moving and dynamic for agents to keep up. With serverless and containers becoming more popular, traditional security solutions that rely on agents are struggling to keep up. For example, an agent on a server may only be able to scan new code when it is deployed, but with serverless, new code can be deployed hundreds or even thousands of times a day. This means that any vulnerabilities in the new code may not be detected until it is too late.
Another reason agent-based scanning is becoming less relevant is that it is often impractical to deploy agents on all machines in a modern cloud environment. This is because there are often too many machines to be feasible to deploy an agent on each one. It is also often not possible to deploy agents on all of the machines in a cloud environment because some of them may be ephemeral, such as containers that only exist for a short period of time.
Modern security solutions take snapshots of production environments and attach them to vendor-managed compute to scan them offline without any operational challenges. This allows them to scan the environment quickly and effectively without needing agents on all machines. It also allows them to scan ephemeral machines, such as containers that would otherwise be inaccessible.
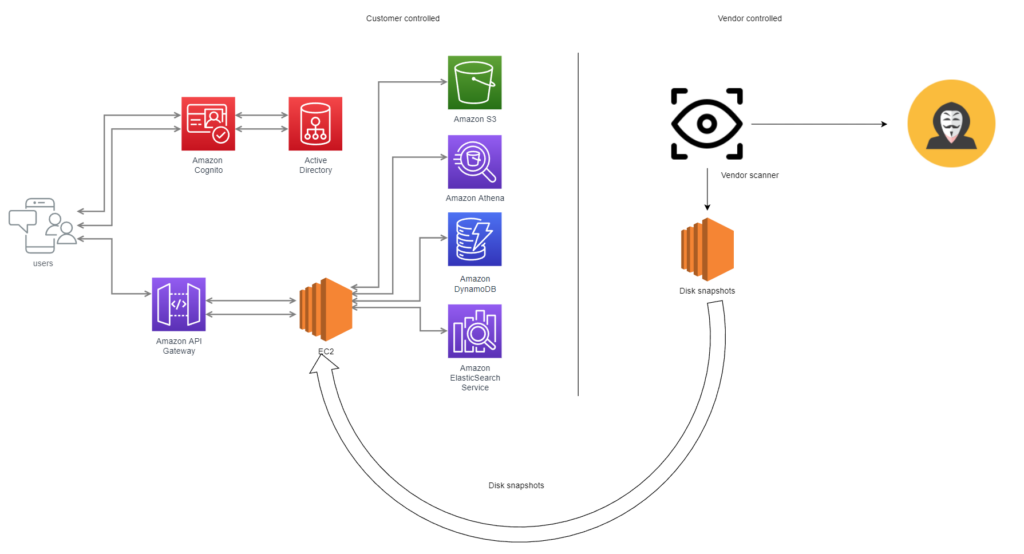
One major risk with offline scanning is that it is opaque and entirely managed by the vendors. This means that it is not always clear how the scans are being performed or what data is being collected, how its managed, and where it’s stored.
Disk snapshots include sensitive information in clear text format. The sensitive data may include customer Personally Identifiable Information (PII) or environmental variables that are secrets and connection strings in clear text.
Exposure to highly sensitive data entails several risks such as exposure, data leakage, data exfiltration, and unauthorized operator access.
You can control the offline environments where scanning takes place. This should ideally happen with your cloud accounts, allowing you to regulate ingress and egress to minimize data-exfiltration risks.
Vendor Components should be scanned for any supply chain vulnerabilities.
To begin with, choose stateless computing instances or workloads that don’t save sensitive data to the disk.
Make use of transparent Policy-As-Code platforms like Prancer, which give you complete control over scanning rules.
