Prancer Enterprise is proud to present the “Autonomous Security” feature, a powerful tool designed to streamline the security assessment process for your company’s cyber assets. Let’s explore how this feature allows Prancer to do the heavy lifting for your security assessments, simplifying your workflows and amplifying your cyber resilience.
To activate the Autonomous Security feature, Customer needs to provide some basic initial information. This includes:
A connection to the cloud provider. This allows the Autonomous Security to read the resources and configurations directly from your cloud provider.
The public domain name of your company.
Connections to the code repositories for both application code and infrastructure code.
With this information, the Autonomous Security system can begin its work.
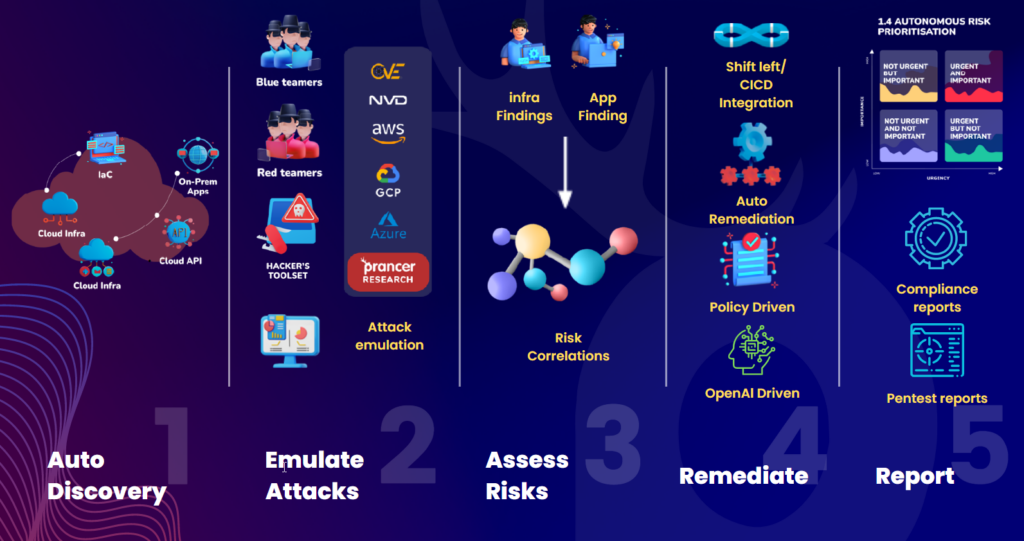
Next, the Prancer crawler engine connects to your cloud provider, code repos and retrieves all resources and configurations. The engine understands the type of each resource and determines the kind of security assessment needed for that resource. The system thus builds an inventory of your cloud resources and continuously updates it for dynamic and up-to-date security analysis.
Leveraging OSINT (Open Source Intelligence), the Prancer engine can identify all subdomains, related public resources, and available APIs based on the initial information gathered.
In this step, Prancer performs a comprehensive security assessment of your applications and infrastructure. This includes:
Attack surface analysis: Prancer performs attack surface analysis from the perspective of an attacker, identifying potential attack vectors that an attacker could gain access to a system or network and formulating attack stories for each application or service type. This helps organizations to improve their security posture and reduce their risk of attack.
Code Security: Prancer performs a comprehensive code analysis of your application and infrastructure as code repositories. This analysis looks for security vulnerabilities, coding errors, and other potential security issues.
Supply chain Security: Prancer performs a supply chain analysis of the opensource software packages used in your applications and infrastructure. This analysis looks for known vulnerabilities in the software packages and identifies any potential security risks.
Threat emulation: Prancer emulates various threat scenarios to test the security of your applications and infrastructure. This includes simulating attacks from both internal and external threats.
Prancer conducts a risk assessment on the identified vulnerabilities and prioritizes them based on CVSS scoring and other metrics. Each finding is linked to the MITRE ATT&CK framework for proper categorization of vulnerabilities. A remediation plan is provided for each alert and finding, along with a validation method.
Prancer’s Autonomous Security provides comprehensive reporting for each attack surface. The system connects the dots and leverages an AI engine to perform an in-depth analysis of the findings. This ensures your team has the most accurate, actionable, and detailed insight into your cyber assets’ security posture.
With Prancer’s Autonomous Security feature, you have a powerful, automated tool at your disposal, designed to give you the edge in managing your company’s cyber security landscape. By integrating this tool into your security strategies, you’re empowered to ensure a more secure, reliable, and compliant infrastructure.